
Ian usually just told lawyers to switch it off and switch it on again.
Allen & Overy has until Tuesday to pay off a gang of cybercriminals or they will release a cache of files stolen from the firm, the hackers have said.
Three weeks ago the LockBit ransomware group announced that it had added the Magic Circle to its long list of victims, which includes Accenture and the Ministry of Defence, and that A&O had until 28 November to pay up.
LockBit originated in countries which belonged to the former Soviet Union and operates as a franchise, providing its software and negotiation framework to affiliates in exchange for a proportion of the ransoms they extort.
Recently the LockBit high table ordered its affiliates to hike the amounts they demand from victims after reportedly being disappointed with the size of ransom payments.
For organisations with revenues upwards of $1 billion, a ransom equating to 0.1% to 3% of the total should be sought, according to a cyberthreat analyst’s report on the gang’s new rates.
That didn’t pan out when an offshoot attempted to extort £66m from Royal Mail. Demands for a sum equivalent to 0.5% of the company’s global revenue faltered when Royal Mail’s negotiator argued that LockBit had actually hacked a loss-making subsidiary of the Plc, Royal Mail International, and that “under no circumstances” would it pay “the absurd amount of money” LockBit had demanded.

On top of which, said Royal Mail’s negotiator, what damage the hack could do had already been done, having triggered a breakdown of the company's ability to make international deliveries.
Allen & Overy’s revenues were £2.1 billion in 2022, which means if the gang is operating in line with LockBit’s edicts, the firm could currently be attempting to argue down a number between £2.1m and £10.5m.
A&O declined to specify how much the criminals were demanding and whether it was engaging with them, referring RollOnFriday to its statement at the time of the attack when it said it had "experienced a data incident impacting a small number of storage servers”.
LockBit’s ransomware can enter a network via phishing, where an employee receives an email requesting access details which appears to have been sent by a benign contact, or via brute force through attacks on servers.
Once inside, the malware self-replicates, simultaneously encrypting files and exfiltrating copies to the LockBit operators.
Affected files are renamed with an appended file-extension of “.lockbit”, and wallpaper on the impacted network’s computers is replaced with a warning informing the user that their files have been stolen, and inviting them to betray their company and provide more information in return for a cut of the ransom.
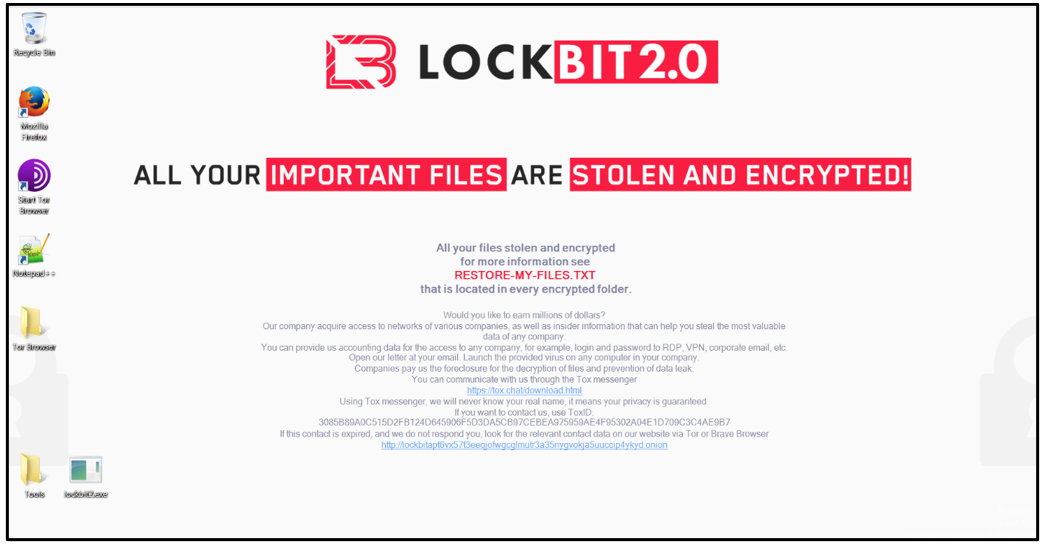
Opening any of the locked files brings up a ransom note which gives directions to LockBit’s ‘Support’ desk to commence negotiations.
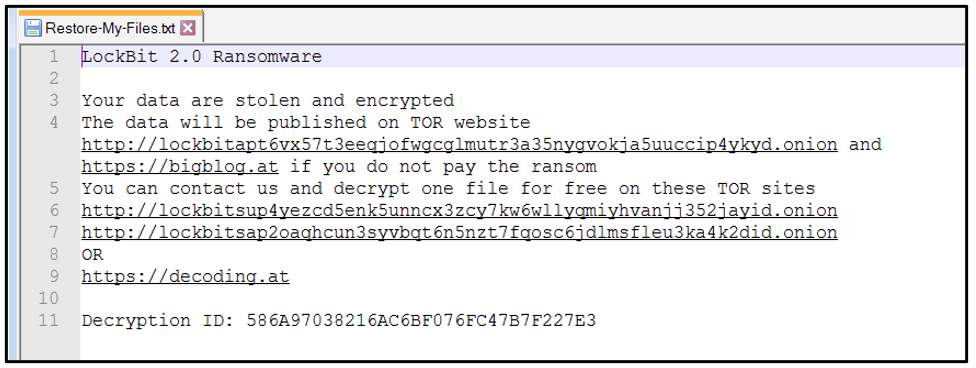
A&O's experience may have varied slightly from this, however, as the firm was infiltrated by the updated Lockbit 3.0, aka 'LockBit Black', according to a source.
Allen & Overy said investigations “to date” had found that its core systems, including email and document management system, were unaffected and that it was operating “normally with some disruption arising from steps taken to contain the incident”.
“Detailed cyber forensic work continues to investigate and remediate the incident. As a matter of priority, we are assessing exactly what data has been impacted, and we are informing affected clients", it said.













Comments
22
8
I have seen the future and this is it
Expect these problems to increase by algebraic functions with AI
I can see firms ditching the internet altogether and returning to pre internet working
20
11
Absolute mega-lols at the huge brass balls on the chap from Royal Mail International.
I'd high five him; but the force from his vast muscular forearms would no doubt shatter every bone in my hand, even were he to engage with just a fraction of his true strength.
17
7
One think you can guarantee is that Allen and Overy's market leading litigation team is going to sue the pant off these crooks.
22
6
Couldn't happen to a nicer firm.
If only there was value in doing this to Facebook, Instagram et al and people's eyes were forced away from their phones and back to the world.... Wouldn't everything be so much nicer.
17
9
@ Dave Graham 24 November 23 09:43
Yes, they'll conduct litigation through smoke signals and morse codes. Firms which are located a few miles out of the City will struggle unfortunately and will have to resort to messenger pigeons.
18
8
Hahaha great banter.
15
11
Time to clear out IT management ?
14
10
Patch yours software, kids, it’s not rocket science, this vulnerability was announced in August.
18
6
A&O are quite happy for their employees to have their apps/emails etcs on people’s personal iPads and iPhones. Major red flag 🚩!!!! What people do on their personal items is a major security risk. One might enjoy surfing the deep/dark web…(it’s not illegal) but has massive consequences.
17
6
@anomynous: No bring your own device at A&O for almost a decade now. What are you talking?